Advancing Confidential Computing with Intel's Project Amber
In this article
The following article is content provided by Intel.
Authors: Nikhil Deshpande, Senior Director of Security and Chief Business Strategist for Project Amber in the Office of the CTO, Intel; & Raghu Yeluri, Sr. Principal Engineer and Lead Security Architect in the Office of the CTO/Security Architecture and Technology Group, Intel.
In just a few short years, confidential computing has gained wide attention and momentum as a powerful new way to provide end-to-end protection of in-use code and data. Financial services, government, retail, healthcare, cloud service providers (CSPs) and many others, especially in regulated industries, are piloting and adopting this emerging security paradigm. So, too, are a wide variety of companies eager to protect the valuable intellectual property of machine learning and artificial intelligence models running in multi-tenant environments.
According to the Everest Group, this "next frontier in data security … is poised for exponential growth."[1] The global market, $1.9 billion in 2021, is expected to grow at a compounded annual rate of 40% - 95% through 2026, the research firm says, driven by cloud and security projects. Many believe that over the next decade confidential computing will become an everyday norm for organizations that manage sensitive, competitive, personally identifiable, and regulated data.
For that to happen, confidential computing must continue to evolve. Specifically, next-generation forms of trust are needed to match the major, quickening shifts in computing infrastructure and enterprise usage, notably multi-cloud, hybrid cloud, and edge computing.
Since the start, Intel has been committed to the advancement of confidential computing. The company is a founding member of The Confidential Computing Consortium, a collaborative project community at the Linux Foundation. Today, our new security service, code-named Project Amber, is working with enterprises, CSPs, systems integrators, independent software vendors (ISVs) and other partners to develop and bring the latest innovation of confidential computing security to organizations worldwide.
To understand what's needed to reach this next level of maturity, and how Intel is driving game-changing innovation of a key component, let's begin with a quick explanation of how things currently work.
How confidential computing gets confidential today
Confidential computing is the protection of data in use by performing computation in a safe, hardware-based enclave. The aim is for data and code loaded into a Trusted Execution Environment (TEE) to be protected against tampering by malicious agents present on the hardware platform. Isolated and secure environments prevent unauthorized access and modification of in-memory applications and data, thereby increasing assurances that the data remains secure.
Historically, the trustworthiness of the TEE comes via a mechanism called attestation. Through attestation, the TEE can provide evidence or measurements of its origin and current state. Both can be verified by another party, which can then decide, programmatically or manually, whether to trust the code running in the TEE.
What's needed next?
While the current approach is useful, it has its limitations. In our view, three key advances are required to truly evaluate the trustworthiness of a TEE, including: independent attestation; uniform, portable attestation; and policy verification:
Independent attestation
In traditional cloud service architectures, the attestation assurance needed for confidential computing typically comes from the cloud service provider. However, many enterprises today are adopting "separation of duties," both as an IT best practice and as an audit and control standard. Key goals are to reduce the risk of malicious or inadvertent breaches of system security, protect data integrity, and prevent disruption of normal business processes. A major requirement under such a model is that a single entity should not control all parts of a transaction or business process. Thus, moving from a model of "self-attestation" by the infrastructure provider to one of independent attestation by a neutral third-party has become an increasingly crucial factor in the decision process for the "cloudification" of sensitive workloads.
Uniform, portable attestation
Many CSPs, ISVs, and solution providers are building their own attestation solutions for workloads running in their infrastructure, on their software. As their customers increasingly adopt multi-cloud and hybrid clouds in addition to their on-premises enterprise networks, the need for uniform, consistent and portable attestation coverage across a variety of vendors and environments grows more relevant.
Policy verification
Finally, attestation assurance is crucial, but it's only one component of establishing trustworthiness in confidential computing. Enterprise leaders say it's imperative for auditing and compliance purposes that workload-specific policies also can be verified.
Intel's solution: Project Amber
Project Amber, as it is referred to within Intel, is a codename project that is designed to meet these requirements. The cornerstone is unlinking attestation from the infrastructure vendor. Instead, a third-party provides the attestation assurance to the workload owner. It's analogous to certificate authorities that assert identity independently, regardless of where the application runs. This crucial architectural independence opens the door to Project Amber's vendor-agnostic security service. The aim is to deliver an independent, transparent, and auditable service that increases trustworthiness with service level agreement (SLA) delivering, initially, three-nines support (99.9% up-time).
Figure 1, below, shows the Project Amber deployment architecture. The TEE-enabled platform and the workload running in the TEE can attest to Project Amber and be verified, regardless of where (cloud, edge, on-prem), and how the workload is deployed (containers, VMs, etc.)
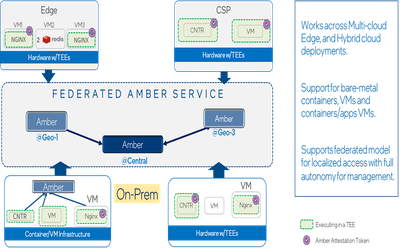
Project Amber can help with one of the most common use cases in confidential computing – deploying an AI model in the cloud. These models are well-trained with datasets by the workload owner. The owners typically consider the AI models as extremely valuable intellectual property and would need them to be protected from theft and compromise at the service provider. Confidential computing provides the natural compute environment in which to deploy these AI models in a public cloud setting, with the benefits of private cloud security.
Figure 2 provides an overview of how Project Amber works:
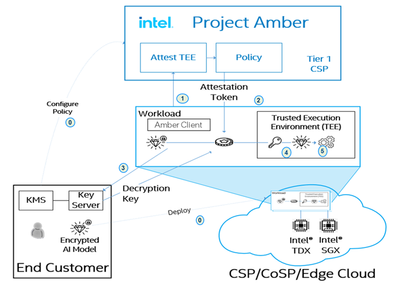
Project Amber client libraries are integrated into the workload prior to its deployment into the cloud. These libraries provide the abstractions and "glue" to communicate with a Project Amber endpoint, providing the evidence of TEE security state and identity. The AI workload is encrypted; decryption keys are in the control of the workload owner. As the workload begins executing, Project Amber is contacted for verification and provides a signed attestation token if attestation is successful. The workload passes the attestation token to the key server inside the customer control center. There, the signature of the token is verified to ensure that it is a genuine Project Amber token. If so, claims in the token are verified. If acceptable, an encryption key is released, wrapped in a way that it can only be unwrapped within the TEE, which exposes the decryption key necessary to decrypt and execute the AI workload.
A win-win for enterprises and industry
Independent, operationally neutral third-party attestation and policy verification offers several major benefits for confidential computing, including:
- Vendor-agnostic support of workloads
- Ability to extend attestation from TEEs to devices, platforms, and supply chains
For enterprises, independent attestation makes it possible to scale and move workloads across a wider range of on-prem, cloud environments and cloud providers, without being tied to a single vendor's verification method. Such attestation mobility can be especially useful in heavily regulated geographies and markets, for example.
Multi-party confidential computing – such as banks sharing anonymized customer data for fraud analysis – will also benefit by the increased security and trust provided by independent, verifiable attestation. In on-prem, or hybrid clouds, Project Amber can help enable separation of business lines required by regulation.
For the industry, third-party verification liberates CSPs and other infrastructure providers from the need to build and maintain complex, expensive attestation systems. Project Amber is not just for hyperscalers; it allows vendors of any size to compete because Intel enables them to scale with Project Amber as a trust provider and they can focus on their core value as a CSP.
Join the Project Amber Pilot Program
Smart organizations today understand that protecting data is essential to extracting its value. As computing moves to span multiple environments – from on-prem to public cloud to edge – organizations need advanced protection controls that help safeguard sensitive IP and workload data wherever the data resides.
Intel is using its advanced technological know-how and foundational position in the industry to extend its leadership in confidential computing. No company, however, can do it alone. Project Amber has evolved in collaboration with a number of customers and partners. Now, we're in a position to cast a wider net and pilot the solution to further refine and optimize Project Amber's capabilities and market model.
If you're an enterprise, cloud service or infrastructure provider, ISV, or systems integrator interested in cloud-based or on-prem confidential computing deployment, please contact us at ProjectAmber@intel.com to learn how you might be able to participate in the Project Amber pilot program.
The next chapter of cloud computing promises that many workloads previously judged too sensitive due to security or regulatory compliance concerns now can take advantage of the cost, accessibility, and flexibility of cloud services. We invite you to join us in innovating what's next.
Sources:
[1] Source: "Confidential Computing – The Next Frontier in Data Security," Everest Group, 2021.
Notices and Disclaimers:
Intel technologies may require enabled hardware, software or service activation.
No product or component can be absolutely secure. Your costs and results may vary.
Intel is committed to respecting human rights and avoiding complicity in human rights abuses. See Intel's Global Human Rights Principles. Intel's products and software are intended only to be used in applications that do not cause or contribute to a violation of an internationally recognized human right.
© Intel Corporation. Intel, the Intel logo, and other Intel marks are trademarks of Intel Corporation or its subsidiaries. Other names and brands may be claimed as the property of others.