Partner POV | 5,000 Fake Microsoft Emails that Your Employees Could Fall For
In this article
This article was written and contributed by our partner, Check Point.
EXECUTIVE SUMMARY:
In the technology sector, Microsoft stands out as the one of the most frequently impersonated brands. Scammers commonly pose as Microsoft employees or affiliated vendors, deceiving email recipients. According to the latest research findings from Harmony Email & Collaboration, this trend is accelerating.
More than 5,000 spoofed Microsoft notifications have been identified by Harmony Email & Collaboration's cyber security researchers.
Across the past month, Harmony Email & Collaboration's cyber security researchers have caught over 5,000 emails masquerading as Microsoft notifications. The emails utilize exceptionally sophisticated obfuscation techniques, rendering it nearly impossible for users to distinguish them from legitimate communications.
The business implications are significant, as email compromise could lead to email account takeover, ransomware, information theft or other negative outcomes.
What's happening
The fake Microsoft emails don't originate from private or unknown domains — a clue that the emails are potential threats. Rather, the emails appear to come from organizational domains impersonating legitimate administrators.
The main portion of a given email will typically include a fake login page or portal, where malicious content may be hidden. An unsuspecting user can easily click on this and input sensitive information or download a threat.
To hide the malicious intent of these emails, cyber criminals are deploying sophisticated obfuscation techniques. Some emails include copied-and-pasted Microsoft privacy policy statements, contributing to an authentic 'look and feel'.
Other emails have links to Microsoft or Bing pages, making it even more challenging for traditional security systems to recognize and mitigate these threats effectively.
Click here to read more about How Email Scams Got Smart
Example
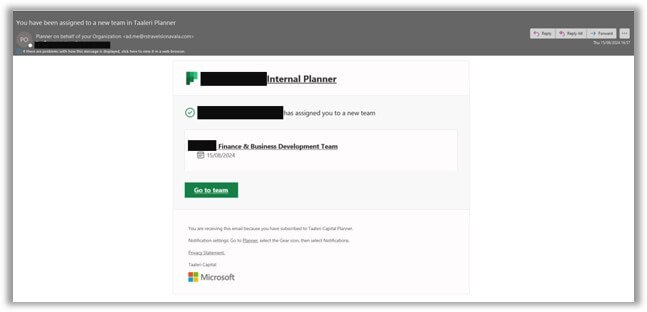
In the email shown below, a cyber criminal has spoofed a Microsoft email and also impersonated an organization's business administrator, sending a (fake) email on the administrator's behalf.
The email looks believable. In particular, the style of the email is so duplicative of what users generally receive that a given user would have no reason to flag it.
The language is perfect. The style is familiar. The graphics look impeccable. So, what should organizations do?
Mitigations
There are measures that organizations can take to sidestep these email-based threats. They include:
- User awareness training. This requires a mention, although generative AI-based text means that users can no longer rely on grammatical errors and stylistic inconsistencies as primary indicators of social engineering.
- AI-powered email security. This stops the full spectrum of inbox incursions. AI-powered email security tools leverage behavioral analysis and machine learning in order to prevent email spoofing, phishing, BEC threats and more.
- Software patching. Organizations should keep all software up-to-date, as to prevent cyber criminals from exploiting any bugs that could allow for easy email spoofing or disruption.

