Partner POV | Akamai Doubles Down on API Security
In this article
This article was written and contributed by our partner, Akamai.
On June 24, we closed our acquisition of Noname Security, and we are excited to share our plans for advancing the protection of APIs. Noname Security is one of the top API security vendors in the market, and this acquisition will accelerate our ability to meet growing customer demand and market requirements.
Specifically, Akamai will be able to extend intelligence across API traffic locations and accommodate whatever business, integration, or deployment requirements our customers may have.
We are integrating the best of the Noname API Security and of Akamai API Security to create a unified product: Akamai API Security.
Why API security is so important
The use of APIs is exploding. They power our world and our experiences of the world. Every day, as we use our devices, our favorite applications are communicating with multiple APIs to do everything from our social media, our shopping, our banking, and checking on our kids in daycare. We use APIs when we work from home when communicating with our company's applications and services.
APIs are used in nearly every industry vertical in the world, driven by business initiatives such as digital transformation, mobile and Internet of Things (IoT) adoption, and open banking. APIs are used in B2B and B2C to enable business in our economy at large. Nearly every business that writes modern applications uses APIs to power those applications, as well as for cross-business services integration.
APIs are attractive to attackers
As a result, APIs are one of the most attractive vectors for attackers. Akamai's data shows that API attacks are increasing at 109% year over year. In a 2023 report, 78% of customers said that they have experienced an API-related security incident in the last 12 months. The security of APIs is an accelerating priority, and Akamai is doubling down on API protections for our customers.
Akamai's acquisition of Noname Security allows us to accelerate the already amazing 200% growth we've had in customer demand for Akamai API Security. Both Akamai and Noname are recognized Leaders in this space, and this acquisition gives us the additional capabilities needed to become the pacesetter in API security.
Why a WAAP solution is not enough
Web application and API protection (WAAP) platforms play an important role in defending web apps and APIs from classes of attacks like those in the OWASP API Security Top 10. But they aren't solving the whole problem.
Other vendors would have you believe that WAAPs can solve all types of API attacks, but the reality is that most WAAP solutions fall short of providing the visibility and depth of API security that's needed to defend against attacks, especially abuse attacks. That is because a WAAP solution does not have the contextual awareness to understand the conversation between API requests and responses.
Web applications and APIs are not the same
This is not surprising given that APIs operate differently from a web application. In a web application, the business logic behind the web app is hidden, but an API's business logic can be exposed directly to the internet, leaving it open to abuse. An example of this was shared in a May 2024 TechCrunch article. A WAAP platform could not have mitigated this type of attack.
That's one reason why Akamai has made significant investments to advance our API security solution, and why we are continuing to push for more innovation and API protections with this latest acquisition.
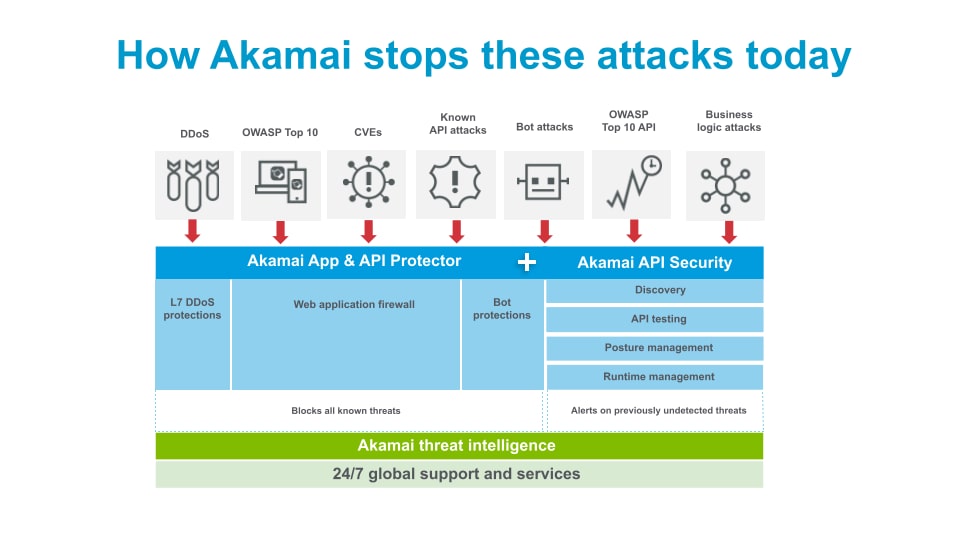
Better together: How WAAP and API security solutions work together to protect APIs
Akamai API Security solves several critical issues
Akamai API Security addresses many of the types of attacks now specified in the OWASP API Security Top 10 that lead to revenue loss, reputational damage, information exposure, and compliance violations.
Our API security solution solves several critical issues, including visibility of the API landscape, detection and blocking of threats and anomalies, and active testing of APIs.
Visibility of the API landscape
As the adage goes: You can't protect what you can't see. Many companies aren't even aware of how many APIs they truly have, so it becomes difficult to quantify their risk. Akamai API Security starts with assessing how many APIs a customer has, and not just those in active use that they are aware of, but even the legacy, shadow, or rogue APIs that they aren't aware of or cannot see. Noname Security's data suggests that their API security platform customers discover, on average, 40% more APIs in their environment than they originally anticipated.
Detection and blocking of threats and anomalies
API Security uses machine learning to detect and identify all kinds of API vulnerabilities and abuse, including data tampering, leakage, misconfigurations, policy violations, behavioral anomalies, and direct API security attacks.
Active testing of APIs
Shift left testing is a critical component of application development, which brings security in from the start. But, until now, APIs were unable to be tested while they were being developed. With API Security, we can incorporate API testing into the CI/CD pipeline to ensure that issues are resolved before the API is released into production.
The added value of Noname
The addition of Noname Security, one of the market leaders in API security, will instantly expand the protections Akamai API Security offers our customers. With Noname's breadth of integrations and deployment choices, we can now offer support across the vendor landscape.
Whether an organization uses the cloud, edge-native, on-premises, or other vendor platforms, Akamai API Security can secure the API environment. With the addition of the Noname solution, Akamai will have the reach and coverage needed to deliver comprehensive API protection for customers across all environments.
We're also excited to add:
Flexible deployment capabilities — deploys rapidly across cloud-hosted, self-hosted, hybrid, and distributed instances
Critical enterprise capabilities — includes role-based access control, self-service configuration, CI/CD integration, dashboards, and advanced automated responses
No data boundary challenges — analyzes data from the attack in memory, which ensures that your data never leaves your environment
More integrations — provides the industry's most comprehensive collection of integrations, including NGINX, AWS, Azure, F5, Apigee, MuleSoft, GCP, and many more; integration with what you already have is important, and this solution ensures comprehensive coverage
Robust API testing — focuses on finding and remediating API security vulnerabilities integrated in the CI/CD pipeline (during the development phase of the software development lifecycle) before they can be exploited
Combining our strengths into one product
As noted, our plan is to combine our current API security innovations with the Noname security solution. The unified solution will provide comprehensive API protection for customers across all environments.
Our integration process will focus on three areas:
- Connection from the Akamai edge network
- Connection into App & API Protector
- Threat intelligence
Connection from the Akamai edge platform
Akamai operates one of the largest private networks in the world. It's the platform from which the majority of our services are delivered, including our market-leading security services (such as App & API Protector and Prolexic DDoS protection), our market-leading content delivery network (CDN), and our public cloud services. Our enterprise customers love how easy it is to use services directly from our platform, so we will be providing integration of Noname into our network for ease of deployment. We expect that integration to be completed three weeks from acquisition.
Connection into App & API Protector
App & API Protector is the industry's best WAAP platform as evidenced by being named a 2024 Customers' Choice for Cloud WAAP for the fifth consecutive year on Gartner® Peer Insights™ and by other analyst reviews. This connection will enable behavioral intelligence generated by Noname to trigger WAAP rules in App & API Protector to automatically block the connection.
Threat intelligence
Akamai collects and analyzes more than 788 terabytes of data every day. All that data is generated by the enormous volume of attacks we see across the predominantly enterprise customer base we serve (we see more than 12 billion web attacks every quarter). That data, along with 200+ security researchers working with it, provides us with incredible threat intelligence. And we are going to integrate that data feed into Akamai API Security, as we do in all our products.

