Partner POV | Introducing Easy API Security Deployment
In this article
- Go from implementation to production in one step
- 5 benefits of using the native connector
- How do Akamai customers benefit from the native connector?
- How do you deploy API Security?
- Why did Akamai build the native connector into API Security and not use EdgeWorkers?
- Protect against vulnerabilities
- Better together with Akamai App & API Protector
- Download
This article was written and contributed by our partner, Akamai.
For those seeking to strengthen your security posture by strategically adding Akamai API Security to your tech stack, this news is for you. With the press of a button, our native connector now integrates API Security directly with Akamai Connected Cloud.

As a result, any Akamai customer using content delivery and at least one security product (i.e., any web application firewall, Kona Site Defender, App & API Protector, Bot Manager Premier, or Account Protector configuration) can integrate their traffic with Akamai API Security.
Because API Security discovers and audits APIs and monitors API activity using behavioral analytics, it is the best solution to detect and respond to API sprawl and API abuse. API Security helps you protect against the OWASP Top 10 list for API vulnerabilities.
While the native connector makes it seamless to integrate with Akamai Connected Cloud, API Security supports all platforms (i.e., all CDNs, API gateways, and cloud environments).
Go from implementation to production in one step
Performing data acquisition integration for many solutions that protect APIs can take anywhere from hours to weeks and typically requires multiple people from the customer organization.
But now, with the click of a button, the native connector sends a copy of your API traffic data from Akamai into the API Security product that powers our detection and response capabilities. Go from implementation to production in one step with no risk or adverse effects.
Although other API security solutions have built their own integrations with the Akamai content delivery network (CDN), Akamai's native connector is the only integration that was directly designed and built by Akamai with continuous support.
Can you purchase API Security if you're not an existing Akamai customer?
API Security also works without the Akamai CDN and can connect with other technologies like any web application firewall, CDN, API gateway, or other reverse proxy through its library of connectors.
5 benefits of using the native connector
Our integration is unique and unlike any other kind of integration from other API security providers. Our integration offers five benefits that other solutions do not:
- Forge ahead with zero-touch deployment
Existing customers who are using Akamai delivery services that have a security configuration don't need to do anything else. With the click of a button, users can activate the connector immediately in production without any risk or adverse effects. There's no on-premises node to deploy.
- Eliminate implementation projects
Instead of funding a team, reshuffling priorities, finding resources, or timing the project, you can choose the route using the native connector, which eliminates the need for those variables and resources.
- Avoid infrastructure and networking costs
The native connector is included as part of the API security solution and requires no extra on-premises infrastructure or any additional workload costs. We also offer a data lake that stores your API traffic data for analysis that eliminates the need to store that data elsewhere.
- Avoid lost or delayed visibility
There is no need for any additional technology or workarounds. Because the connector is fully out-of-band and completely integrated with Akamai API Security, the work has already been done for you. Plus, this is an extension of Akamai's existing infrastructure, which means you save time with a prebuilt solution.
- Forget about maintenance
As part of Akamai API Security, the connector will be fully supported and enhanced alongside the product itself. You won't have to worry about adapting it to your workflows as your organization evolves, starting from day one.
How do Akamai customers benefit from the native connector?
With integration from the connector, API Security is now accessible through the Akamai Control Center (ACC). This means that only users that have the connector will gain Akamai-authorized access into API activity.
Akamai customers benefit from zero-touch deployment, avoiding any implementation time, risk, effort, cost, and maintenance — all within the ACC.
How do you deploy API Security?
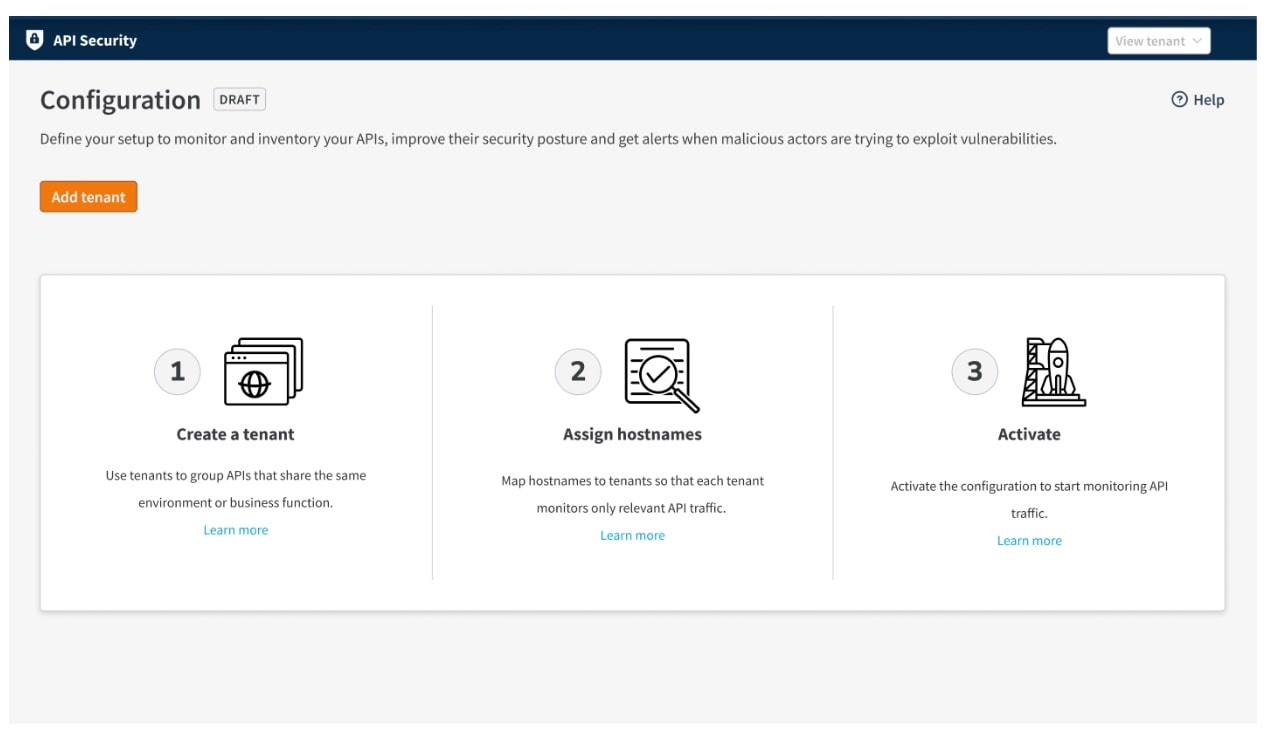
API Security is a 100% software-as-a-service solution that you can deploy instantly with no on-premises node required for the native connector. The time from deployment to activation is 20 to 30 minutes.
Simply create a tenant, assign hostnames to that tenant, and then click an activate button (Figure). That's as complicated as it gets: Three easy steps to deploy API Security.
Why did Akamai build the native connector into API Security and not use EdgeWorkers?
Akamai engineering recommends the native connector as a best practice, no-code, fully supported option for integrating API Security. If you want a full-code, self-supported solution, you can use Akamai EdgeWorkers; just note that it may be subject to edge compute limits.
How do I benefit from the native connector being integrated directly into API Security?
With API Security, we've done the building for you — so we can offer a unified solution. To ensure that you maintain full visibility of your traffic across solutions, we strongly recommend using API Security instead of other solutions that rely on EdgeWorkers.
Protect against vulnerabilities
API Security uses behavioral analytics rooted in extended detection and response (XDR) techniques to provide detection and response capabilities that prevent business logic abuse. It also protects against the OWASP API Security Top 10 vulnerabilities.
Better together with Akamai App & API Protector
API Security complements our flagship web application and API protection offering, Akamai App & API Protector, which protects websites, applications, and APIs by blocking incoming malicious traffic in real time. With leading bot, distributed denial-of-service (DDoS), and API protections, App & API Protector helps solve for the OWASP Top 10 vulnerabilities for web applications.
Together, API Security and App & API Protector deliver the most comprehensive global protection, combining enterprise-wide visibility, behavioral analysis of API activity, and the prevention of attacks and abuse.

