Partner POV | Reducing Your Attack Surface With Existing Endpoint Security Tools
In this article
This article was written and contributed by our partner, Trellix.
Over the last decade we've seen the pendulum swing from "all data must be stored within the logical [and sometimes physical] boundaries of an organization" to "hurry up and get everything in the cloud!" As with all major swings, we're starting to see the pendulum settle somewhere in the middle, with cloud repatriation happening as organizations see cloud billing costs rise. This is forcing everyone to step back and operate where it makes the most sense for the application and use case, whether that's on prem or in the cloud. Frequently it's both.
The outcome: a growing attack surface that needs to be managed.
Two essential components for managing the expanding attack surface are endpoint security and policy management. By addressing vulnerabilities at endpoints and enforcing robust policies, organizations can mitigate risks and prevent breaches more effectively.
Easier said than done.
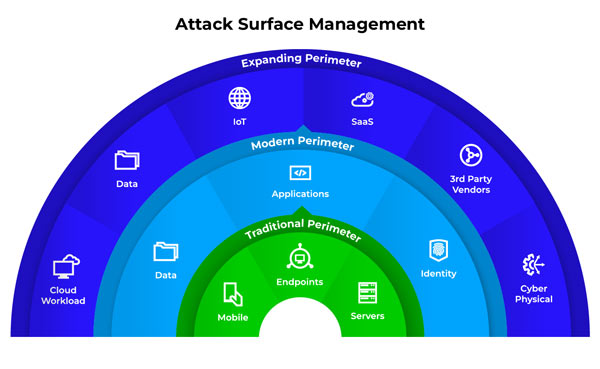
What is the attack surface?
The attack surface refers to all the possible points where an attacker can gain unauthorized access to a system. This includes endpoints like laptops, servers, smartphones, and IoT devices, as well as software inventory, network configurations, cloud infrastructure, and user behavior. Minimizing the attack surface reduces the opportunities for cybercriminals to exploit weaknesses.
Endpoint security processes and technologies
Endpoints are the last mile of defense, yet a prime target for attackers. There's a whole bunch of ways to secure endpoints, and here are a few processes and technologies you should implement:
- Antivirus and Anti-malware Protection: Prevent malicious software and processes from executing.
- Endpoint Detection and Response (EDR): Provide real-time monitoring, detection, and response to threats.
- Application Allow & Deny Lists: Limit software that can run on endpoints to known, validated, and trusted applications. Ideal for environments that change very little, such as Industrial Control Systems.
- Patch Management: Regularly update software to fix known vulnerabilities. Detecting misconfigurations, unpatched systems, or outdated software versions on exposed assets is good hygiene to reduce your attack surface. Automate this process with software such as Trellix Policy Auditor .
- Asset Management: Asset discovery, classification and vulnerability identification (which informs the patching process). This is a feature of most network security tools including Network Detection and Response, as well as many open source tools such as Zenmap and Cacti exist as well.
- Device Encryption: Ensure sensitive data remains secure even if devices are lost or stolen.
Endpoint Policy management is critical
A well-defined security policy framework ensures consistent protection across all endpoints and organizational layers. Effective policy management includes:
- Protection Policies: Define levels of protection for corporate assets, applications, and systems based on criticality. Servers and laptops have different needs, and likely should have different types of protection. Use the protection policy to define, audit, and enforce the policy.
- Access Control Policies: Define who can access specific systems and data. This can be done with ePolicy Orchestrator, as well as some identity & access management (IAM) systems.
- Device Restriction: Implement policies to restrict the transfer and storage of data. This includes any removable media such as USB based devices, as well as through wireless protocols such as Bluetooth. Where possible, use device management tools to disable USB and Bluetooth entirely on systems that don't need them.
- Data Protection Policies: Specify how sensitive data should be stored, accessed, and shared.
- Regular Audits and Compliance: Whether you have to meet a specific regulatory compliance requirement (ie: PCI, NIS2, DORA, etc.) or simply adhere to corporate requirements, you'll need a way to ensure the established policies align with industry regulations and best practices. Automate this process with software such as Trellix Policy Auditor.
Endpoint security + policy management = attack surface reduction
By integrating policy management with robust endpoint security, organizations can gain a unified view of security – and adherence to compliance requirements – across all endpoints. This visibility helps identify gaps and enforce changes rapidly. Additionally, dynamic policy adjustments based on behavioral analytics can adapt policies in real time based on detected threats or suspicious behavior. For example, if a user suddenly logs into an application from outside the country outside of work hours, the policy can dynamically remove them from the application. This type of dynamic decision making is an ideal use case to be solved by artificial intelligence.
Best practices for reducing the attack surface
To maximize the effectiveness of combined endpoint security and policy management:
- Limit administrative privileges to required administrators.
- Monitor highly privileged accounts. These are targets for compromise.
- Conduct regular vulnerability assessments, software and OS patching
- Train employees on cybersecurity awareness. Phishing evaluations still work.
- Deploy multi-factor authentication (MFA) across systems where possible.
- Maintain an up-to-date inventory of all devices and software.
- Practice network segmentation. Isolate critical systems to limit lateral movement in the event of a breach.
- Eliminate unnecessary services and decommission old assets.
The bottom line
Reducing the increasingly dynamic attack surface requires a proactive approach that combines robust endpoint security with effective policy management. By continuously assessing risks, leveraging technology, and enforcing strong policies, we've seen customers strengthen cybersecurity programs with a focus on prevention and subsequently putting less work on security analysts.

